

With over 2.6 million applications to account for in the Play Store, Google is constantly at war with fraudulent and malicious apps plaguing their ecosystem. At the same time, Google tries to promote high-quality apps for users to enjoy, although sometimes the apps they select are of dubious quality. Cheetah Mobile is perhaps one of the most infamous development companies among our users because of their practice of collecting data on users and serving tons of sketchy advertisements. Their acquisition of QuickPic led many XDA members to scramble for an alternative to the once highly-recommended gallery app. But despite the poor quality of Cheetah Mobile’s products, we never had any reason to suspect them of anything truly malicious – until now. The latest research from Kochava has provided evidence that several Android apps from Cheetah Mobile, and one from Kika, are engaging in ad fraud.
Some background
Cheetah Mobile, while best known for developing applications on Android, is a company that actually focuses on selling data. They don’t hide this fact at all, though it’s something that many users are oblivious to. However, it’s hard for users to tell exactly how Cheetah Mobile is using the data they collect. Clean Master, an application by CM with more than 1 billion downloads, has access to permissions like Play Install Referrer API, network connection details, activity recognition, retrieving running apps, and many more which are not at all required for cleaning the cache on a device. As it turns out, all of the above permissions are actually being used as part of an ad fraud scheme.
Kika Keyboard is a popular third-party keyboard app on the Play Store with over 200 million downloads, according to AppBrain. Kika Keyboard is not owned by Cheetah Mobile, but the app has also been found to engage in similar ad fraud schemes.
Ad fraud
To recoup the costs of development, some developers generate revenue by placing advertisements in their applications. Developers can sometimes get a bonus for referring users to install other applications displayed in the ads. The bonus can vary from $0.50 to $3.00, typically. The system works like this: You display an advertisement showing another application, the user downloads the sponsored application and runs it, then the application which sponsored the ad will award a bonus to the referring app developer. Kochava has demonstrated that Cheetah Mobile has been tricking applications into thinking that they should be the recipient of bonuses for referrals when in reality CM’s apps played no role in referring the user to download an application. This nets CM money both from Google and the developers who monetized their app via advertisements. Here is how the ad referral process typically (left picture) versus a hijacked ad referral process (right picture). Images courtesy of BuzzFeed News.
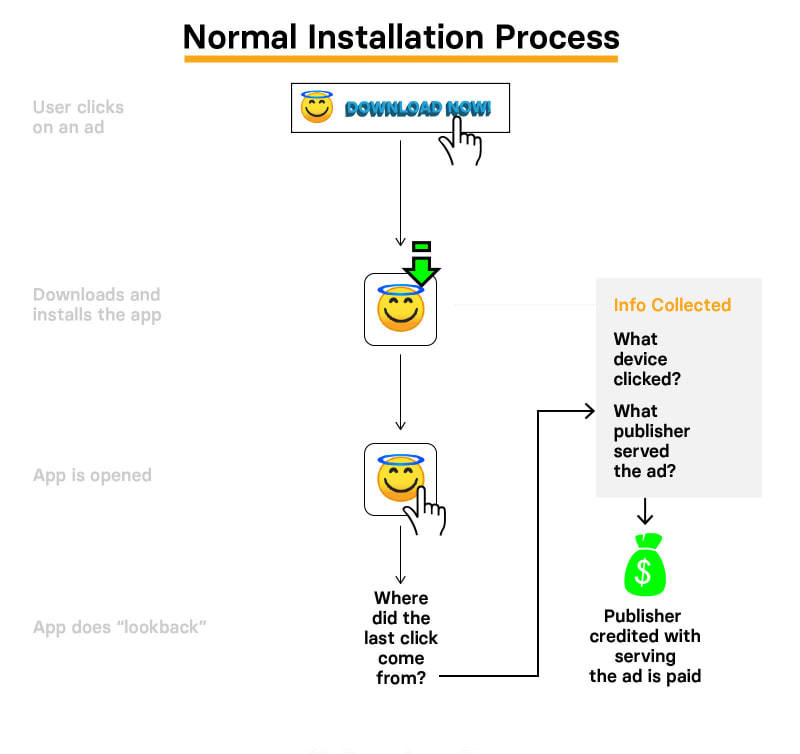

This is made possible by tricking the Google Play Install Referrer API, which CM Master and most of CM’s apps have access to. The research also showed that Cheetah Mobile mostly uses in-house developed libraries and APIs in their applications as part of this ad fraud scheme.
Affected apps
Here is a list of the apps that were caught participating in the fraudulent ad scheme. If you have any of them installed on any of your Android devices, we recommend uninstalling them immediately.
- Clean Master
- Security Master
- CM Launcher 3D
- Kika Keyboard (owned by Kika Tech)
- Battery Doctor
- Cheetah Keyboard
- CM Locker
- CM File Manager
What’s alarming is that some of the biggest device manufacturers in the world have used these applications in the past. For example, Samsung promotes Clean Master by implementing it in Samsung Experience and guiding users about installing the app. Microsoft has partnered with Cheetah Mobile to implement Cortana, the company’s digital assistant, in CM Launcher 3D.
Conclusion
Just as you’ve always suspected, Cheetah Mobile’s main interest is in selling your data. But they’ve now been shown to go above and beyond in abusing the permissions granted to their apps. The ad fraud scheme abuses user trust and steals revenue from not only Google but also developers that should be receiving the referral bonus in the first place. We hope that Google continues their investigatation of these apps, and if they corroborate Kochava’s findings, to remove them from the Play Store. As for users, we recommend you uninstall the apps listed in the previous section while keeping in mind that the list may not be comprehensive. To keep your device secure, make sure to always check the permissions an application is requesting and do some research on the team behind the app.
If you wish to read the statements offered by both Cheetah Mobile and Kika, follow the link below to the original Buzzfeed News report.
Source: BuzzFeed


0 comments:
Post a Comment